Security Principles for Hackers: Part 2
Welcome back, my curious hacker friends!
In our last tutorial, we explored the fundamental CIA and DAD triads that form the foundation of security thinking. Today, we're taking it to the next level with some advanced security concepts that will help you understand how the big players build their defenses – and more importantly, how you can find the cracks in their armor.
Defense-in-Depth: Why Security Pros Don't Put All Their Eggs in One Basket
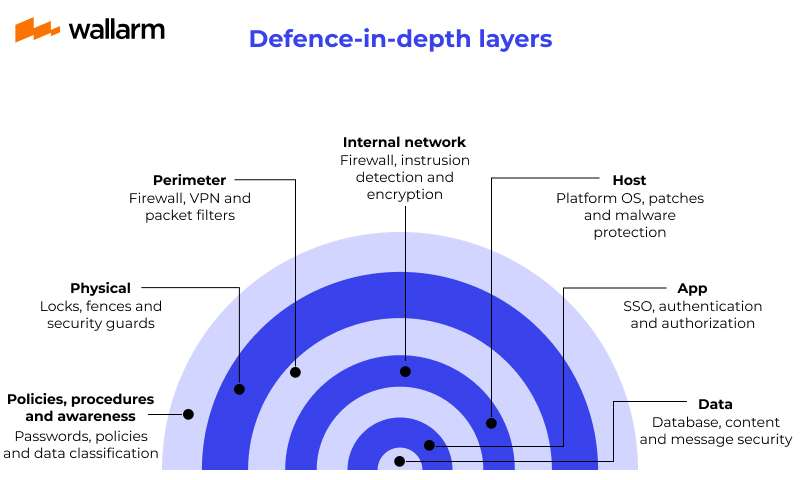
If there's one security principle that keeps hackers up at night, it's Defense-in-Depth. Also called Multi-Level Security, this is the digital equivalent of a medieval castle with multiple defensive layers – moat, walls, guards, and keep.
Let me break this down with an example we can all relate to: your personal computer.
Think about it – would you protect all your sensitive data, cryptocurrency wallets, and personal photos with just a single password? I think not! A proper security setup looks more like this:
- Strong password to lock your computer (something better than "password123," please)
- Two-factor authentication for your critical accounts
- Firewall filtering suspicious network traffic
- Encryption on sensitive files
As a hacker, when planning an attack, always assume multiple layers of defense and map out how you'll defeat each one.
ISO/IEC 19249: How the Security Bigwigs Think
Ever wonder how major organizations approach security? The International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) created ISO/IEC 19249 – a fancy framework of architectural and design principles for building secure systems.
I know, I know – standards documents are boring. But as a hacker, understanding these principles gives you insight into how your targets are thinking. Let's break down the good stuff:
The Five Architectural Principles Every Hacker Should Know
1. Domain Separation
This principle is all about not keeping all the goodies in one place. Systems separate components into distinct domains, each with their own security controls. For example, operating systems separate user-mode applications from kernel-mode operations.
Hacker's perspective: Look for trust relationships between domains. The bridges between separate domains are often your best attack vectors.
2. Layering
Layering structures security into multiple levels, with each enforcing its own policies. Take web applications:
- Firewalls filter incoming traffic
- Web servers process HTTP requests
- Application logic handles business rules
- Databases enforce access controls
Hacker's perspective: Analyze each layer separately.
3. Encapsulation
Encapsulation hides implementation details and restricts access to internal components. Think of mobile banking apps that interact only through specific APIs, preventing direct database access.
Hacker's perspective: Look for ways to bypass the intended interfaces. API vulnerabilities, memory leaks, and side-channel attacks can all crack open encapsulated systems.
4. Redundancy
Redundancy improves availability by creating backups of critical components. Cloud services replicate data across multiple servers. RAID systems distribute data across multiple drives.
Hacker's perspective: Redundancy can sometimes create consistency issues. If you can't take down all redundant systems, look for ways to exploit differences between them.
5. Virtualization
Virtualization creates isolated environments on shared hardware. Cloud providers use it to separate customer workloads. Virtual machines and containers sandbox potentially harmful applications.
Hacker's perspective: VM escapes and container breakouts are high-value targets. Also look for misconfigured virtualizations that leak information between environments.
Five Design Principles That Create (or Break) Security
1. Least Privilege: You Can't Hack What You Can't Access
Systems should restrict access to the minimum necessary permissions. Your HR rep can view payroll records but not modify them. Regular users can't install software. Admins have separate accounts for administrative tasks.
Hacker's perspective: Privilege escalation is your friend. Look for overlooked permissions, improperly secured configuration files, or services running with excessive privileges.
2. Attack Surface Minimization: Fewer Doors, Fewer Break-ins
Reducing entry points makes systems more secure. Those IoT devices with unnecessary services enabled? They're a hacker's paradise. Proper hardening disables everything not explicitly needed.
Hacker's perspective: Scan for uncommon ports and services. Organizations often forget about legacy systems or development interfaces that bypass main security controls.
3. Centralized Parameter Validation: The Input Sanitizer
Many exploits (SQL injection, buffer overflows, XSS) leverage unvalidated input. Strong systems validate all input centrally before processing.
Hacker's perspective: Test parameter validation at different entry points. Often validation is inconsistent, especially in complex systems built over time by different teams.
4. Centralized Security Services: Single Point of Security (and Failure)
Security functions should be managed centrally – think single sign-on (SSO) for authentication across multiple applications.
Hacker's perspective: These central services are high-value targets. Compromise the authentication server, and you get keys to the whole kingdom.
5. Error and Exception Handling: Failing Gracefully (or Not)
Systems need to handle unexpected failures safely. ATMs should never dispense cash when in error states. Web applications shouldn't expose database details in error messages.
Hacker's perspective: Error messages are information gold mines. Force errors through unexpected inputs and watch how the system handles them – it often reveals implementation details.
Trust Models: To Trust or Not to Trust?
Now let's talk about one of the most fascinating aspects of security: trust. There are two competing philosophies here, and understanding them is crucial for any serious hacker:
Trust but Verify: The Old School Approach
This principle says, "I'll trust you, but I'm still watching your every move." Organizations implementing this approach set up extensive logging and monitoring. They trust their users and systems but verify that everything remains normal.
Hacker's perspective: Look for monitoring blind spots. What actions aren't being logged? Which logs aren't being reviewed? These are your stealth pathways.
Zero Trust: The New Security Hotness
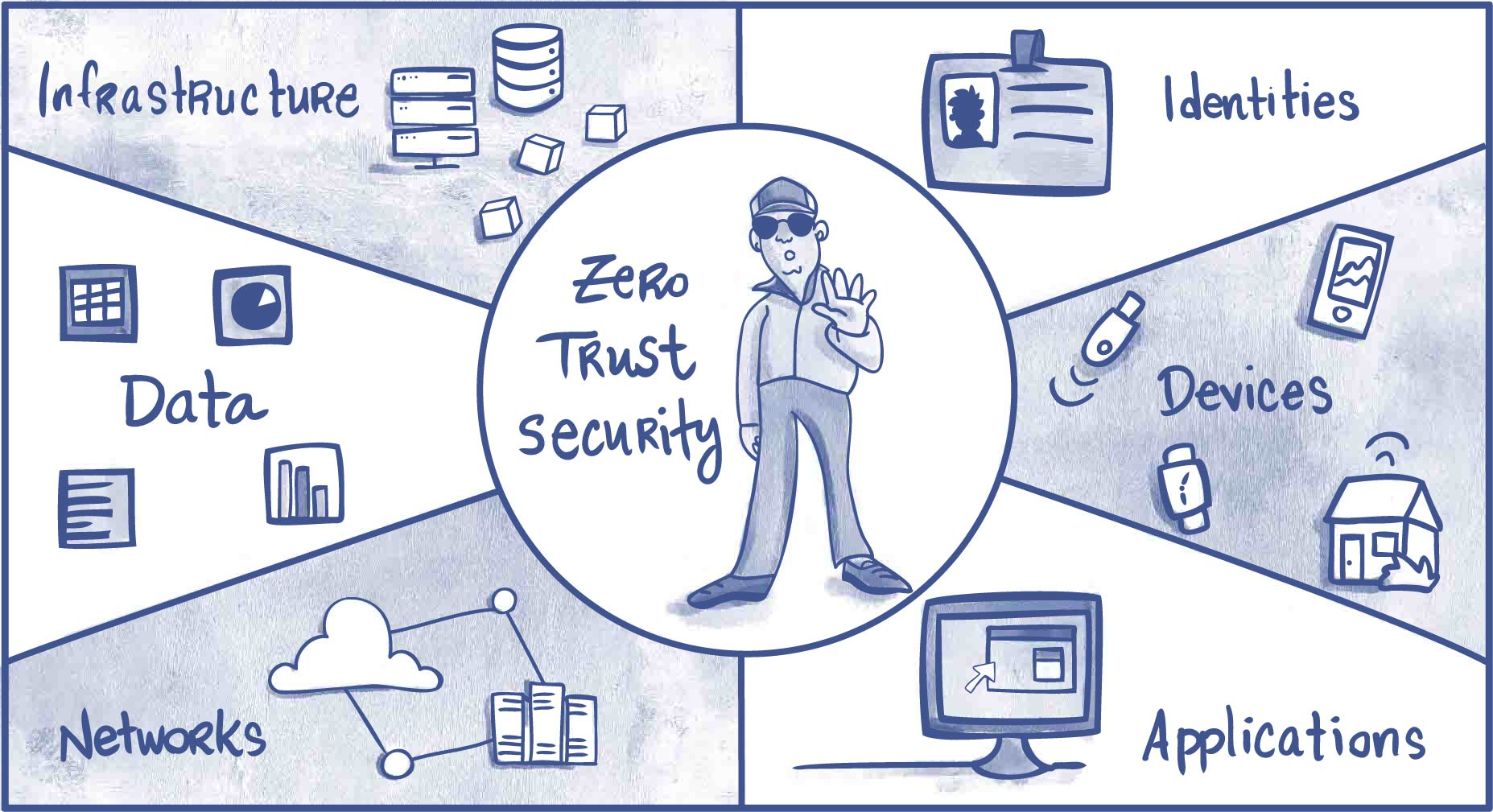
Zero Trust takes a more paranoid approach: "Never trust, always verify." It treats trust itself as a vulnerability and tries to eliminate it entirely.
In Zero Trust:
- Your network location doesn't matter
- Every device, user, and application must authenticate
- Authorization is required for every resource access
- Authentication is continuous, not just at login
One key implementation is microsegmentation, where network segments can be as small as a single host, and all communication between segments requires authentication.
Hacker's perspective: Zero Trust makes lateral movement much harder. Focus on compromising authentication mechanisms themselves or look for legacy systems that aren't fully integrated into the Zero Trust architecture.
The Reality Check
Here's some practical wisdom: there's always a limit to how much security an organization can implement before it starts harming their business. Perfect security means zero usability.
As a hacker, you're looking for that sweet spot where security was sacrificed for convenience. Maybe it's the executive who demanded an exception to the security policy. Perhaps it's the legacy system that's "too critical" to update. Or maybe it's just the overworked admin who took shortcuts.
Conclusion
Security isn't static – it's an ongoing battle between attackers and defenders. What worked yesterday might not work tomorrow. The ISO principles give you insight into how organizations are thinking, but remember that theory and practice often differ wildly.
Keep studying, stay ethical, and remember – understanding how systems are secured is the first step to finding their weaknesses.
Happy (ethical) hacking!


