Russian APT28 Deploys "NotDoor" Backdoor Through Microsoft Outlook

Welcome back, aspiring hackers!
It’s Aircorridor here.
Nation-state actors continue to develop sophisticated tools to infiltrate and maintain access to their targets' networks. One of the most concerning developments in recent weeks has been the discovery of a new backdoor called "NotDoor," deployed by the Russian state-sponsored group APT28 (also known as Fancy Bear) against organizations in NATO member countries.
The NotDoor backdoor changes how attackers use normal business software to carry out cyberattacks. Instead of installing typical malware, the group APT28 has turned Microsoft Outlook itself into a hidden tool for communication and control.
NotDoor is an Outlook VBA macro that watches for emails with a special trigger word. When it sees one, it lets the attacker steal data, upload files, and run commands on the victim’s computer. Because these actions look like normal email activity, they’re very hard for security systems to spot.
What Makes NotDoor Different from Traditional Backdoors

NotDoor is fundamentally different from conventional backdoors in several key ways:
Legitimate Application Abuse: Rather than installing standalone malware, NotDoor operates through Visual Basic for Applications (VBA) macros within Microsoft Outlook, making it appear as legitimate functionality to both users and security tools.
Email-Triggered Activation: The backdoor remains dormant until it receives emails containing specific trigger words. This passive approach significantly reduces its detectability footprint compared to backdoors that maintain persistent network connections.
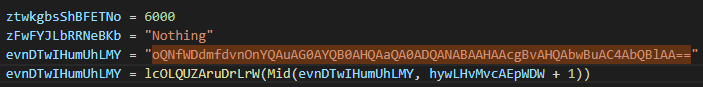
Advanced Evasion Techniques: The malware employs sophisticated obfuscation methods, including custom string encoding that prepends random alphanumeric characters to valid Base64 strings, creating the illusion of encryption.
DLL Sideloading: The deployment mechanism leverages a legitimate signed Microsoft OneDrive executable to load a malicious SSPICLI.dll, bypassing security controls that typically block unsigned executables.
The NotDoor Infection Chain
Understanding how NotDoor operates is essential for developing effective countermeasures. Let's examine each phase of the attack:
Phase 1: Initial Deployment and Registry Modifications
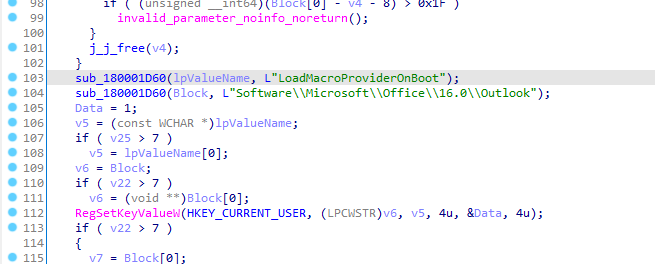
The attack begins with the placement of a file called testtemp.ini in the C:\ProgramData\ directory. The threat actors then execute the legitimate OneDrive.exe binary, which loads a malicious SSPICLI.dll through DLL sideloading.
This malicious DLL performs several critical functions:
- Copies the backdoor payload to
%APPDATA%\Microsoft\Outlook\VbaProject.OTM - Performs DNS and HTTP requests to verify successful installation
- Modifies multiple registry keys to enable macro execution and establish persistence
The registry modifications include:
- Enabling
LoadMacroProviderOnBootinSoftware\Microsoft\Office\16.0\Outlook - Setting macro security level to allow execution via
Software\Microsoft\Office\16.0\Outlook\Security - Disabling security dialogue messages through
Software\Microsoft\Office\16.0\Outlook\Options\General
Phase 2: Backdoor Activation and Monitoring
Once installed, NotDoor leverages Outlook's event system to monitor for incoming emails. The malware hooks into two key events:
Application_MAPILogonComplete: Executes when Outlook startsApplication_NewMailEx: Triggers when new emails arrive
During startup, the backdoor creates a temporary folder at %TEMP%\Temp and checks for any existing files that need to be exfiltrated.
Lab52 found the following:
The project is obfuscated, with variable and function names replaced by random alphabetic strings to conceal its behavior. Additionally, the malware employs a unique string encoding technique for both internal data and dynamically generated strings. This method involves prepending random alphanumeric characters to a valid Base64 string, creating the illusion of encryption when decoded.
Phase 3: Command Execution Through Email
The backdoor monitors incoming emails for trigger words - in the analyzed sample, "Daily Report" serves as the activation phrase. When a trigger email is received, NotDoor:
- Parses the email content to extract encrypted commands
- Deletes the triggering email to remove evidence
- Executes the specified commands
- Sends results back via email
NotDoor's Command Capabilities
The backdoor supports four primary command types:
cmd: Executes system commands and returns output as email attachments
cmdno: Executes commands without returning output
dwn: Downloads (exfiltrates) files from the victim's system
upl: Uploads files to the victim's system
Results are sent to specified email addresses using subjects formatted as "Re: <ID> <EMAIL SUBJECT>", making the communications appear as normal email replies.
Organizational Defense Strategies
Defending against NotDoor requires a multi-layered approach:
Policy Controls
Implement strict macro execution policies and consider disabling VBA macros entirely where not required for business operations.
User Training
Educate users about the risks of enabling macros and the importance of reporting suspicious email behavior.
Network Segmentation
Limit the potential impact of compromised endpoints through proper network segmentation and access controls.
Regular Auditing
Conduct periodic audits of Outlook configurations and installed macros across the organization.
Summary
The NotDoor backdoor represents a significant evolution in APT28's tactics, demonstrating how nation-state actors continue to adapt and find new ways to abuse legitimate business applications. By transforming Microsoft Outlook into a covert communication channel, APT28 has created a backdoor that can operate undetected within normal business operations for extended periods.
The NotDoor campaign demonstrates that advanced persistent threats target all platforms and applications. While we've focused on Windows and Outlook in this analysis, remember that security isn't paranoia—it's preparation. Mac malware is real, and iOS devices face sophisticated threats like Pegasus spyware that have infected tens of thousands of users worldwide.
My comprehensive security guide teaches you to master physical security with FileVault 2 encryption, detect advanced malware with professional tools, harden iPhone security against theft and compromise, and use Amnesty International's MVT toolkit to scan for nation-state spyware like Pegasus. Don't wait until sophisticated threats compromise your systems—every day without proper security is a day your data remains vulnerable.



