Phishing Attacks: Tactics, Threats, and How to Stay Safe Online
Phishing constitutes a major cyber threat, with the potential to exploit human psychology to procure sensitive information through the use of deceptive emails, messages and websites. This article will examine various phishing techniques, including email phishing, spear phishing, smishing and business email compromise (BEC).
Understanding Phishing
Phishing is a cyberattack method that relies heavily on social engineering techniques. Rather than using brute-force hacking or software vulnerabilities, attackers manipulate human psychology to achieve their goals.
Social engineering is a form of deception that exploits trust, fear, urgency, or curiosity to trick individuals into voluntarily providing sensitive information, such as login credentials, banking details, or personal identification data.
Hackers typically pose as legitimate organizations or individuals whom the victim is likely to trust. These entities may include well-known companies such as PayPal, Microsoft, or Amazon, as well as banks, government agencies, or even the victim's employer. The attackers craft emails, messages, or websites that appear genuine, using official logos, domain names that closely resemble legitimate ones, and language that mimics corporate communication styles.
The success of phishing depends on the ability to convince the victim to take a specific action, such as:
- Clicking on a malicious link that leads to a fake website where they unknowingly enter their credentials.
- Downloading an attachment that contains malware, spyware, or ransomware.
- Responding with sensitive information, such as credit card numbers, Social Security numbers, or security codes.
- Authorizing a fraudulent financial transaction, believing it to be a legitimate business request.
Phishing is a form of cybercrime that relies on psychological manipulation rather than technical hacking. This means that even individuals with strong passwords and secure devices can fall victim to it.
To make their messages seem urgent and authentic, cybercriminals will utilize various strategies, such as the following:
- "Your account has been suspended due to suspicious activity."
- "It is imperative that you verify your identity to prevent account deactivation."
Another common tactic is to claim that the recipient has won a prize, such as a contest or a reward, and to urge them to claim their winnings immediately.
- "An invoice is overdue—please process payment immediately."
Given the increasing sophistication of cybercriminals, phishing attacks have evolved into multiple distinct forms, each using different methods to deceive victims and steal information.
Types of Phishing Attacks
Email Phishing
Email phishing is the most prevalent and well-established form of phishing. In this method, attackers send fraudulent emails that appear to originate from trusted organizations, such as banks, online retailers, or service providers.
These emails typically include:
- Fake links directing recipients to counterfeit websites that closely resemble legitimate login pages, prompting them to enter their credentials.
- Malicious attachments that, when opened, install malware on the recipient's device.
- Requests for personal information under the guise of security checks, account verification, or billing issues.
Example of an Email Phishing Attack
A user receives an email that appears to be from PayPal, claiming that their account has been temporarily suspended due to suspicious activity. The email includes an urgent request to "verify their identity" by clicking on a provided link.
Upon clicking the link, the user is redirected to a fraudulent PayPal login page that closely mimics the authentic one—complete with the official logo, colors, and design elements. Believing the request to be genuine, the user enters their email address and password.
As soon as the credentials are entered, they are immediately sent to the attacker, granting them unauthorized access to the victim's PayPal account. In many cases, the fraudulent site may also prompt the victim to enter additional details, such as:
- Security questions
- Credit card information
- Two-factor authentication codes
By the time the user realizes the deception, the attackers may have already:
- Gained access to their actual PayPal account
- Made unauthorized transactions
- Changed the account password, locking the victim out
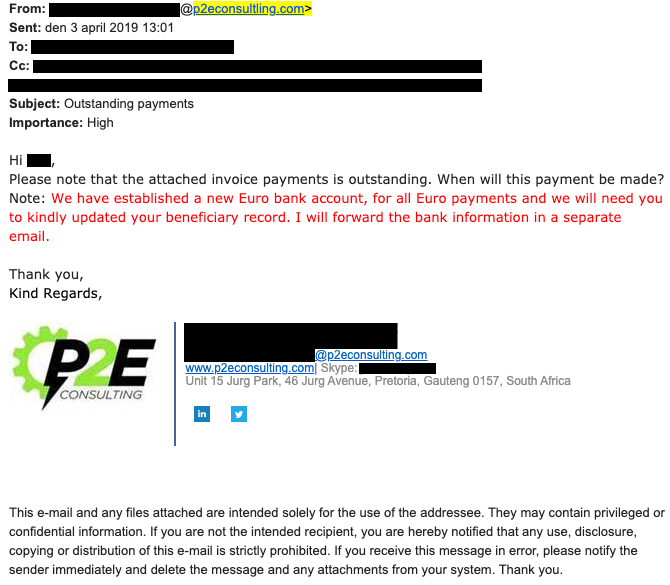
Business Email Compromise (BEC)
Business Email Compromise (BEC) is an advanced form of phishing that specifically targets companies, particularly those involved in financial transactions. Attackers typically gain access to a legitimate business email account through spear phishing (explained below). Once they gain control, they use the compromised account to send fraudulent requests.
Common BEC Scams Include:
- Changing vendor payment details to redirect funds to an attacker-controlled account.
- Authorizing fraudulent wire transfers for fake invoices.
- Requesting confidential business data under the guise of routine company operations.
Example of a BEC Attack
An HR manager at a large corporation receives an email that appears to be from the CEO, requesting a list of all employees’ personal and financial details, including:
- Social Security numbers
- Salary information
- Direct deposit banking details
The email is professionally written, featuring the CEO’s name, email signature, and even their profile picture, making it appear authentic. The message states that the company is conducting a “routine payroll audit” and needs the information urgently.
Believing the request to be legitimate, the HR manager compiles the requested data and sends it back to the email address provided.
However, the email was actually sent by a hacker who had spoofed the CEO’s email address. The stolen employee information is then used for:
- Identity theft
- Fraudulent tax filings
- Unauthorized withdrawals from employee bank accounts
By the time the fraud is detected, many employees may have already suffered financial losses and credit damage.
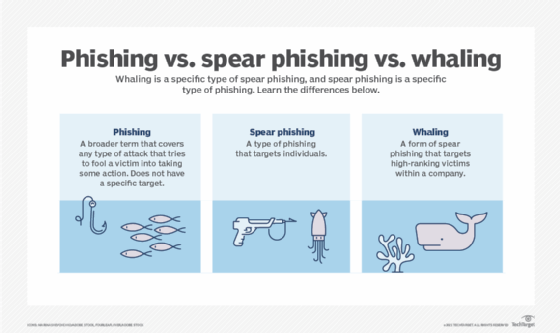
Spear Phishing
Spear phishing is a highly personalized cyberattack aimed at a specific individual or organization. Unlike regular email phishing, which targets a large number of recipients, spear phishing is meticulously crafted for a single victim or a small group of individuals.
Attackers conduct extensive research on their targets using publicly available information, such as:
- Social media profiles
- Company websites
- News articles and press releases
This preparation allows them to craft highly convincing emails that appear authentic and relevant to the recipient.
Example of a Spear Phishing Attack
A marketing executive at a well-known tech company receives an email that appears to be from the company’s cloud storage provider (e.g., Google Drive or Dropbox). The email states that a confidential client report has been shared with them and urges them to click on a link to access the document.
The email looks legitimate, featuring:
- The provider’s official logo and colors
- A familiar email layout
- The name of a real colleague who supposedly shared the document
Trusting the email, the executive clicks the link and is redirected to a fake login page that mimics the actual cloud service provider’s sign-in portal. Without suspicion, they enter their work email and password.
Unbeknownst to them, the credentials are instantly sent to the hacker, who now has access to:
- Confidential client data
- Company marketing strategies
- Sensitive corporate files
Within minutes, the attacker begins exfiltrating valuable corporate information, potentially leading to a data breach and financial loss for the company.
Whaling
Whaling is a specialized form of spear phishing that specifically targets high-ranking individuals within companies or organizations. This method of cyber fraud is particularly sophisticated and high-risk, as it focuses on executives who have access to sensitive corporate data and financial accounts.
Common targets include:
- CEOs (Chief Executive Officers)
- CFOs (Chief Financial Officers)
- Senior Executives
- Government Officials
A successful whaling attack can result in severe financial losses, data breaches, and compromised corporate systems.
How Whaling Attacks Work
Whaling emails are carefully crafted to appear as though they come from trusted sources, such as:
- Other executives within the company
- Legal departments
- Business partners or vendors
These fraudulent emails typically request actions such as:
- Approving a financial transaction
- Providing confidential business documents
- Granting access to corporate systems
Example of a Whaling Attack
A senior accountant at a multinational company receives an email that appears to be from the company’s legal department. The email states that the company is involved in a confidential merger negotiation and that an urgent legal fee payment must be processed to finalize the deal.
The email is highly convincing, featuring:
- Official company letterhead
- Legal terminology
- The name of a real company lawyer
To prevent verification, the message warns that due to the sensitive nature of the transaction, it must be kept strictly confidential.
Attached to the email is:
- A fake invoice for the legal services
- New banking details where the funds should be transferred
By the time the fraud is detected, the funds have already been withdrawn from the fraudulent account, resulting in a significant financial loss for the company.
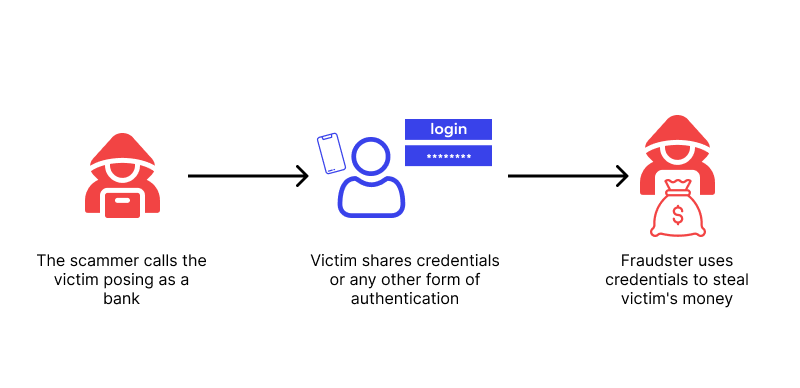
Vishing
Vishing (voice phishing) is a fraudulent scheme that uses phone calls as a medium to deceive victims into revealing sensitive information or making unauthorized payments. Instead of relying on emails or fake websites, vishing scammers manipulate victims through direct verbal communication, often using caller ID spoofing to make the call appear legitimate.
Common Vishing Scams Involve Impersonation of:
- Bank representatives, claiming there has been fraudulent activity on the victim's account.
- Technical support agents, asserting that the victim's computer has been compromised.
- Government officials, warning the victim about unpaid fines or legal issues that require immediate attention.
Key Tactics Used in Vishing Attacks:
- Caller ID spoofing – Manipulating the caller's identity to appear as if the call is from a legitimate organization.
- Fear and urgency – Pressuring the victim to act quickly before verifying the request.
Example of a Vishing Attack
A small business owner receives a phone call from someone claiming to be from their electricity provider. The caller, speaking professionally, informs them that their latest utility payment has not been received and that their business will face immediate power disconnection unless payment is made within the next 30 minutes.
The scammer intensifies the pressure, stating that a technician is already en route to shut off the electricity and that the only way to stop the disconnection is to make an urgent payment via prepaid debit card or wire transfer.
Fearing a disruption to business operations, the owner complies and transfers the money. Only later do they realize that their actual utility bill was paid on time and that they have fallen victim to a vishing scam.
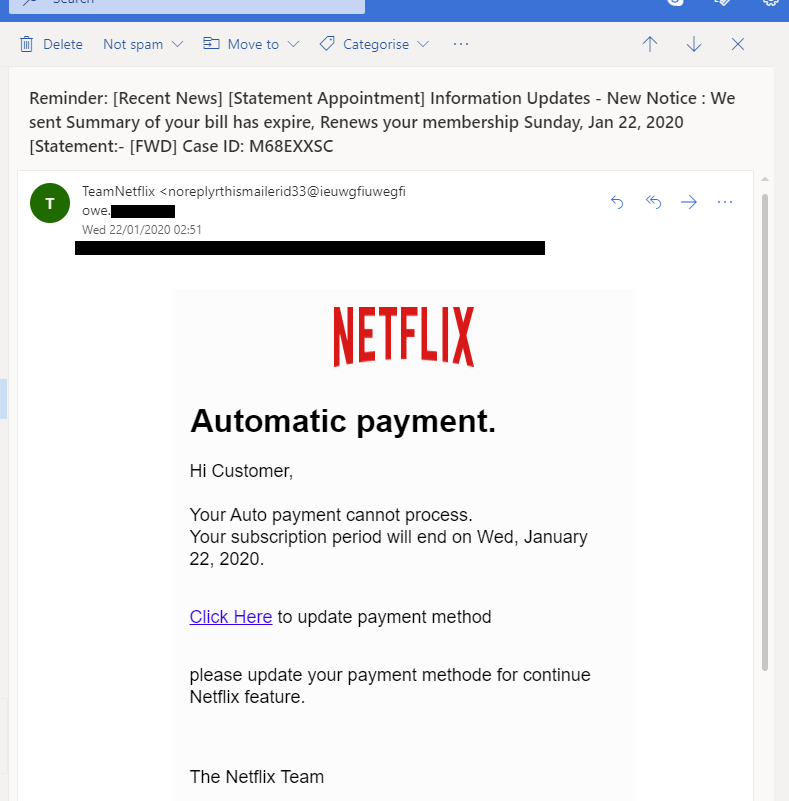
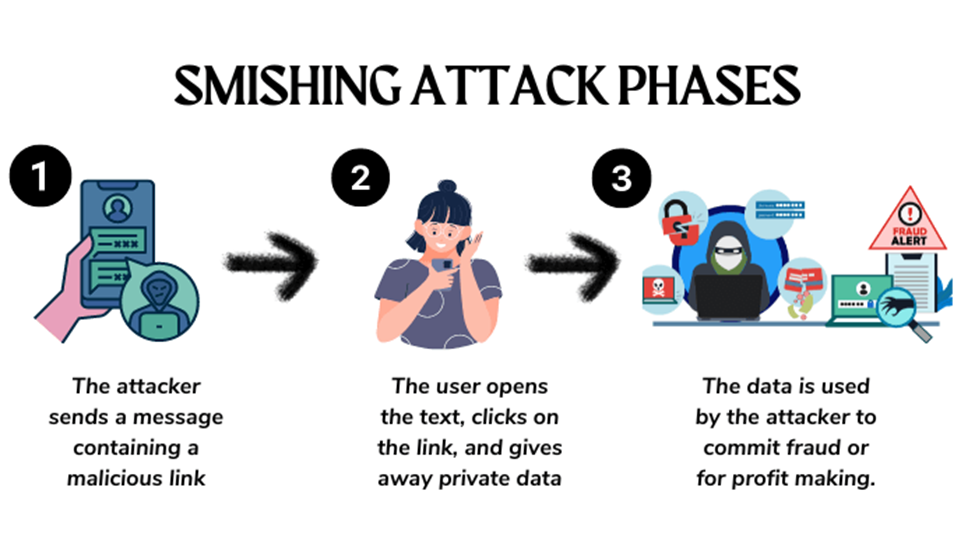
Smishing
Smishing (SMS phishing) is a form of phishing that targets victims through text messages instead of emails. Attackers use urgent messages and malicious links to deceive recipients into revealing sensitive information.
Common Smishing Scams Involve:
- Bank fraud alerts – Messages claiming that the recipient's account has been frozen and requires immediate action.
- Fake delivery notifications – Fraudulent messages prompting users to confirm or reschedule a nonexistent parcel delivery.
- Government scams – Texts warning about tax issues, unpaid fines, or legal consequences to create panic.
Example of a Smishing Attack
A customer receives a text message that appears to be from a well-known delivery service like FedEx or DHL. The message states:
🚨 "Your package could not be delivered due to an address issue. Please update your details here to avoid return: [malicious link]."
Since the victim is expecting a package, they click the link, which takes them to a fake tracking page that closely resembles the legitimate delivery service's website.
The page requests the victim to enter their:
- Full name
- Home address
- Credit card details (to cover a small "redelivery fee")
Believing this to be a standard procedure, the victim provides their information. However, the details are immediately sent to scammers, who:
- Make fraudulent purchases using the stolen credit card.
- Sell the victim’s personal data on the dark web for further exploitation
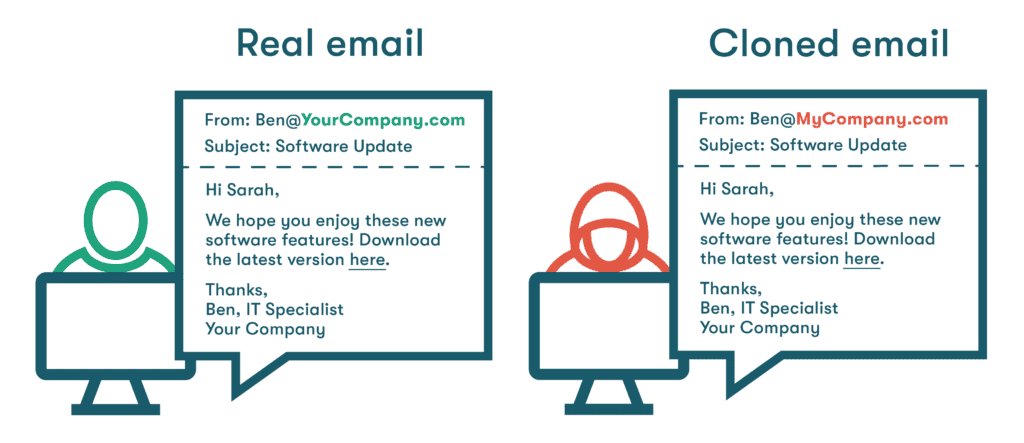
Clone Phishing
Clone phishing is a type of phishing attack where cybercriminals duplicate a legitimate email that the victim has previously received. The attackers replace the original attachments or links with malicious versions, making the email appear familiar and trustworthy. Since the email mimics a legitimate request, the victim is more likely to interact with it.
Example of a Clone Phishing Attack
An employee at a large corporation receives an email that appears to be from the company’s IT support team. The email claims that the company is upgrading its security system and that all employees must install a mandatory security update to protect their accounts from recent cyber threats.
Attached to the email is a file named:
- “Security_Update.exe”
The email urges the employee to download and run the file immediately and warns that failure to install the update could result in restricted access to company systems.
Trusting the request, the employee downloads and executes the file. However, instead of installing a legitimate update, the file:
- Covertly installs spyware that records keystrokes, screenshots, and login credentials.
- This allows hackers to gain unauthorized access to company databases, financial records, and confidential communications.
Protective Measures to Stay Safe from Phishing Attacks
Phishing attacks have grown increasingly sophisticated, requiring proactive security measures from both individuals and organizations. Since phishing exploits human psychology rather than technical vulnerabilities, even the most secure systems can be compromised if users aren't vigilant. Below are effective strategies to protect yourself from phishing threats:
1. Be Skeptical of Emails and Messages
Phishing emails often create a sense of urgency, fear, or excitement to pressure victims into taking quick action. Cybercriminals frequently impersonate trusted organizations, such as banks, government agencies, and tech companies, to gain credibility.
How to Identify a Phishing Email or Message:
- Check the sender’s email address: Phishing emails often use addresses that resemble real ones, with slight variations (e.g., support@paypa1.com instead of support@paypal.com).
- Look for grammatical errors: While not all phishing emails contain mistakes, many do. These errors often stem from bulk emails sent by non-native speakers.
- Avoid clicking on suspicious links: If an email asks you to "verify your account" or "update your password," do not click the link. Instead, visit the website directly by typing the URL in your browser.
- Be cautious with attachments: Do not open attachments from unsolicited emails, as they may contain malware like ransomware or spyware.
2. Verify URLs Before Entering Personal Information
Phishing websites often resemble legitimate ones, with slightly altered URLs designed to deceive users.
How to Identify a Fraudulent Website:
- Hover over links: Before clicking, hover over the link to reveal its true destination. If it looks suspicious, don’t click it.
- Avoid shortened URLs: Links from services like bit.ly or t.co can hide the real destination.
- Manually type URLs: Always type the URL directly into the address bar when accessing sensitive websites (e.g., online banking).
- Check for HTTPS: Ensure the website uses HTTPS for secure connections. While this doesn't guarantee security, most phishing sites lack valid SSL certificates.
3. Keep Software and Antivirus Up to Date
Hackers often exploit security vulnerabilities in outdated software. Phishing emails frequently contain malware that targets unpatched flaws.
Best Practices:
- Enable automatic updates for your operating system, browsers, and security software.
- Use reputable antivirus software (e.g., Bitdefender) to detect and block phishing attempts.
- Update browser security settings to activate phishing protection, with browsers like Google Chrome and Firefox offering built-in protection.
4. Use Multi-Factor Authentication (MFA)
Even if a hacker steals your password, multi-factor authentication (MFA) can add an additional layer of protection to prevent unauthorized access.
How MFA Works:
- One-time codes: Sent via SMS, email, or an authenticator app.
- Biometric authentication: Fingerprint or face recognition.
- Security keys: A physical device required for login.
- Best Practice: Use an authenticator app (e.g., Google Authenticator or Microsoft Authenticator) over SMS codes to protect against SIM-swapping attacks.
5. Use a Password Manager
A password manager (e.g., 1Password or LastPass) can significantly reduce the risk of phishing attacks.
How a Password Manager Helps:
- Generates strong, unique passwords for each account.
- Automatically fills in passwords only on legitimate websites, preventing login credentials from being entered on phishing sites.
- Eliminates password reuse, a common vulnerability that allows hackers to access multiple accounts with one stolen password.
6. Educate Yourself and Others
The biggest vulnerability in cybersecurity is human error. Individuals and organizations must stay informed about the latest phishing tactics to avoid falling victim.
Steps to Stay Educated:
- Undertake cybersecurity awareness training, using platforms like KnowBe4 or PhishMe for phishing simulation exercises.
- Educate family members and colleagues, especially those with limited tech knowledge, on common phishing techniques.
- Be mindful of what personal information you share on social media; cybercriminals use details from platforms like LinkedIn, Facebook, and Instagram to craft convincing spear-phishing attacks.
Conclusion
Phishing remains one of the most prevalent and evolving cyber threats, exploiting human psychology to deceive individuals and organizations into revealing sensitive information. As cybercriminals refine their tactics—leveraging social engineering, impersonation, and even deepfake AI—phishing attacks have become increasingly difficult to detect and prevent.
This article has explored various phishing techniques, including email phishing, spear phishing, whaling, smishing, vishing, clone phishing, and business email compromise (BEC), with real-world examples illustrating their impact. Additionally, it has examined the modern strategies used by attackers, such as spoofed websites, malware distribution, and psychological manipulation through urgency and fear.
To combat phishing, both individuals and organizations must adopt a multi-layered cybersecurity approach. Key protective measures include:
- Verifying the authenticity of emails and avoiding suspicious links.
- Using multi-factor authentication (MFA) for an added security layer.
- Implementing strong, unique passwords and securely storing them in a password manager.
- Keeping software and security systems up to date to prevent exploitation of vulnerabilities.
Moreover, cybersecurity education is essential. Employees and individuals must be trained to recognize and respond to phishing attempts. Additionally, users should avoid conducting sensitive transactions over public Wi-Fi, opting for a VPN when secure browsing is required.
As phishing tactics continue to evolve, vigilance, awareness, and proactive cybersecurity measures are more critical than ever. The best defense against phishing is a combination of technology and informed decision-making. By staying alert, following security best practices, and ensuring ongoing education, individuals and businesses can significantly reduce their risk of falling victim to phishing attacks.
In an era of increasingly sophisticated digital threats, cybersecurity is no longer optional—it is essential.