Pegasus Spyware: The Ultimate Digital Surveillance Tool

Pegasus spyware is one of the most powerful and controversial surveillance tools in the world. Created by the Israeli company NSO Group, it has revolutionized digital surveillance while raising serious concerns about privacy and human rights. This article explores its history, capabilities, and impact.
The Origins of Pegasus
The story of Pegasus begins in 2010 when three Israeli entrepreneurs - Niv Carmi, Omri Lavie, and Shalev Hulio - founded NSO Group Technologies. The company was established with the stated mission of developing technology solutions to help government intelligence and law enforcement agencies combat terrorism and serious crime. However, what emerged from their efforts would become far more significant than initially anticipated.

The development of Pegasus began in earnest around 2011, coinciding with the growing global demand for sophisticated surveillance tools. NSO Group positioned itself as a legitimate provider of surveillance technology, marketing Pegasus exclusively to government agencies and law enforcement organizations. The company maintained that its technology was designed to help track criminals and terrorists, a claim that would later be scrutinized as evidence of broader usage emerged.
Technical Architecture and Capabilities
Pegasus represents the pinnacle of surveillance technology, combining various sophisticated attack vectors with unprecedented access to device functions. At its core, Pegasus is designed to be virtually undetectable while maintaining complete access to a target's device.
The infection process typically begins with sophisticated exploit chains, known as zero-click exploits, which require no interaction from the target. These exploits take advantage of previously unknown vulnerabilities in popular applications and operating systems. Once installed, Pegasus establishes a secure connection to its command and control servers, enabling remote control of the infected device.
The spyware's capabilities are extensive and deeply concerning. It can access and exfiltrate messages, emails, photos, and videos stored on the device. It can activate the camera and microphone remotely, effectively turning the device into a surveillance tool. Pegasus can track location data, record keystrokes, and access encrypted communications from popular messaging apps like WhatsApp, Telegram, and Signal.
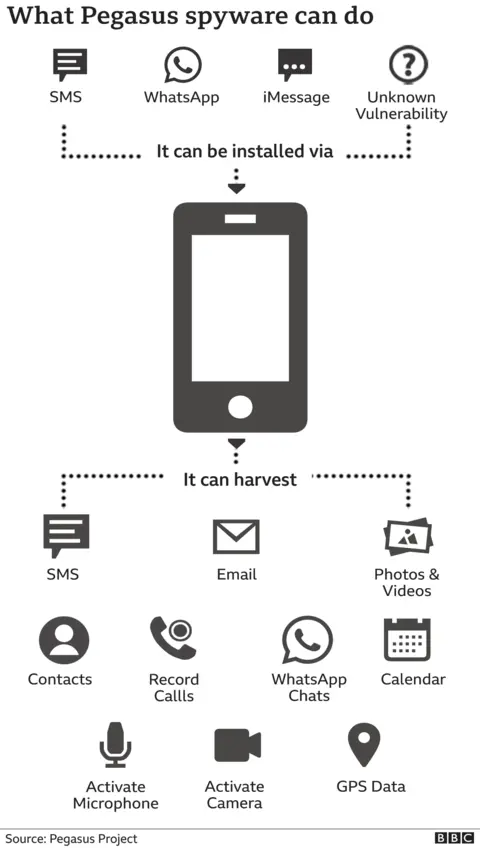
Perhaps most significantly, Pegasus can gather data from applications that are typically considered secure, including encrypted messaging services. It accomplishes this by capturing information before encryption occurs or after decryption, effectively bypassing security measures entirely.
Documented Cases and Global Impact
The global impact of Pegasus became particularly evident in 2021 when the Pegasus Project, a collaborative investigative journalism effort, revealed the extensive use of the spyware against journalists, activists, business executives, and political figures worldwide.
One of the most high-profile cases involved the surveillance of Jeff Bezos, CEO of Amazon, in 2018. Following this incident, forensic analysis suggested that Pegasus had been used to compromise Bezos's phone through a WhatsApp message, leading to significant data exfiltration.
The murder of journalist Jamal Khashoggi in 2018 was also linked to Pegasus surveillance. Investigation revealed that several people close to Khashoggi had been targeted with the spyware, potentially contributing to tracking his movements and communications before his death.
Technical Countermeasures and Detection
Detecting Pegasus infections has proven extremely challenging due to the sophistication of the spyware's stealth mechanisms. However, security researchers and organizations have developed various methods to identify potential infections.
Mobile security experts have identified several indicators of compromise, including unusual battery drain, unexpected device heating, and increased data usage. However, these signs are not definitive proof of infection, as they could be caused by other factors.
More reliable detection methods involve sophisticated forensic analysis of device logs and network traffic patterns. Organizations like Amnesty International have developed tools to analyze device backups for signs of Pegasus infection, though these tools require significant technical expertise to use effectively.
Conclusion
Pegasus spyware represents a watershed moment in the history of digital surveillance. Its sophisticated capabilities, widespread deployment, and the controversy surrounding its use have brought critical issues of privacy, security, and human rights to the forefront of global discourse.
As technology continues to evolve, the lessons learned from Pegasus will likely influence future approaches to surveillance technology regulation, digital security, and privacy protection. The ongoing debate about balancing legitimate security needs with privacy rights and civil liberties remains more relevant than ever.
For users interested in securing their Apple devices and scanning for potential Pegasus infections, we offer a comprehensive guide with detailed steps and best practices. This guide includes advanced security measures, recommended tools, and professional techniques for detecting and preventing spyware infections 👇