Obsidian Basics: Your Digital Brain for Cybersecurity Operations and OSINT Investigations
In our line of work, organizing information is just as critical as gathering it. Whether you're conducting OSINT investigations, documenting vulnerabilities, or planning cyber operations, you need a reliable system to store, connect, and retrieve your findings. This is where Obsidian comes in – a powerful knowledge management tool that can serve as your second brain in the digital battlefield.
As you know, traditional note-taking applications often fall short when dealing with complex, interconnected information. Spreadsheets become unwieldy, text documents get lost in folders, and critical connections between pieces of intelligence remain hidden. For cybersecurity professionals and digital investigators, these limitations can mean the difference between a successful operation and a missed opportunity.
Obsidian offers a different approach to knowledge management – one based on networked thinking and markdown files that you control. Let's dive into how this tool can revolutionize your workflow and enhance your capabilities in cybersecurity operations.
Step #1 Understanding Obsidian's Core Concepts
At its heart, Obsidian is a knowledge base that works on top of a local folder of plain text Markdown files. This seemingly simple foundation provides several immediate advantages for security professionals:
First, your data remains completely under your control. Unlike cloud-based solutions, Obsidian stores everything locally by default. This means sensitive investigation notes never leave your system unless you explicitly choose to sync them.
Second, Obsidian uses plain text Markdown files, ensuring your data remains accessible even if the application itself becomes unavailable. This future-proofs your intelligence gathering and prevents vendor lock-in – critical considerations for long-term operations.
The real power of Obsidian, however, lies in its approach to connections. Rather than organizing notes in a hierarchical folder structure, Obsidian emphasizes linking between notes, creating a network of information that mirrors how our brains actually work.
When you're investigating a threat actor, for example, you can easily link their techniques to similar cases, connect them to infrastructure notes, and reference relevant tools – all without duplicating information or losing context.
Step #2 Comparing Knowledge Management Tools for Security Professionals
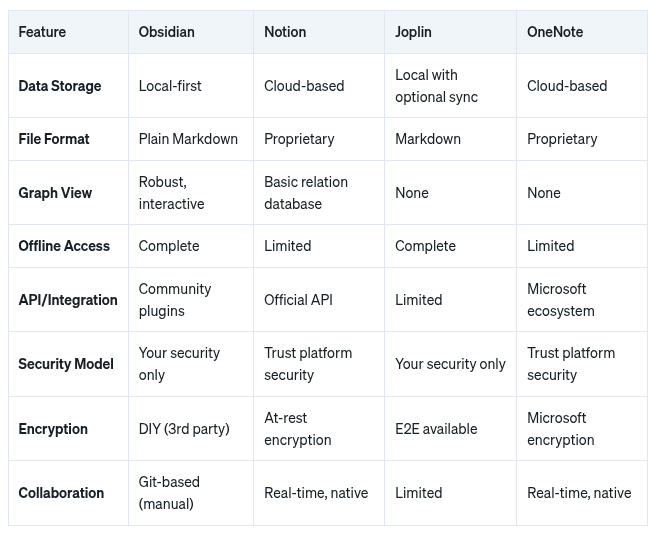
Let's compare Obsidian with other popular alternatives to understand their relative strengths for cybersecurity work.
Notion: Collaboration at a Security Cost
Notion offers an all-in-one workspace with robust collaboration features and polished databases. For security teams working collaboratively, its real-time editing and comprehensive permission system are significant advantages.
Security Considerations:
- Cloud-based storage means your sensitive security data resides on Notion's servers
- Despite their security measures, you must trust their platform security
- Even with encryption at rest, Notion technically has access to your data
- Internet connectivity required for full functionality
Best for: Security teams that prioritize collaboration and integration with other cloud tools, especially for less sensitive information or client-facing documentation.
Joplin: The Open-Source Contender
Joplin combines local storage with open-source transparency, making it a security-conscious alternative to Obsidian.
Security Considerations:
- End-to-end encryption available for synchronization
- Open-source codebase allows for security auditing
- Self-hostable synchronization server option
- Lacks the networked thinking capabilities of Obsidian
Best for: Security professionals who prioritize open-source solutions and need strong encryption guarantees for synchronized notes.
OneNote: Enterprise Integration
Microsoft's OneNote integrates seamlessly with the corporate environment many security professionals work within.
Security Considerations:
- Deep integration with Microsoft security ecosystem
- Enterprise compliance features
- Proprietary format limits control and portability
- Cloud-first approach similar to Notion's security limitations
Best for: Security teams in Microsoft-centric organizations where compliance requirements and existing Microsoft licensing make it a convenient choice.
Why Obsidian Excels for Cybersecurity Operations
For most cybersecurity scenarios, Obsidian's unique combination of features makes it particularly well-suited to our field:
- Local-First Security: By storing files locally by default, Obsidian aligns with the defense-in-depth principle. Your sensitive security information never leaves your system unless you explicitly configure synchronization.
- Plain Text Sovereignty: Unlike proprietary formats, Markdown files remain accessible even if Obsidian itself becomes unavailable—crucial for long-term security documentation.
- Graph Visualization: The interconnected nature of security information (threats, vulnerabilities, systems, etc.) maps perfectly to Obsidian's graph view, revealing relationships that might otherwise remain hidden.
- Customization for Security Workflows: Through plugins and templates, Obsidian can be tailored to security-specific workflows like vulnerability tracking, OSINT investigation, and incident response.
- Controlled Sharing: When collaboration is necessary, you decide exactly how to share your data—whether through selective exports, Git repositories, or third-party synchronization services with appropriate security controls.
Step #3 Setting Up Your Cybersecurity Vault
Let's start by creating a dedicated vault (Obsidian's term for a collection of notes) for your cybersecurity work.
First, download and install Obsidian from their official website. The application is available for Windows, macOS, and Linux, making it versatile across different operating environments.
Once installed, open Obsidian and select "Create new vault."
Name it as you want, in my case, it will be “Cyber Operations”. Choose a secure location on your system – preferably one that's encrypted and regularly backed up.
After creating your vault, you'll be presented with a blank canvas. This is where we'll build our knowledge base.
Step #4 Leveraging Obsidian for OSINT Investigations
OSINT (Open Source Intelligence) investigations benefit tremendously from Obsidian's capabilities. Let's explore how to structure an OSINT investigation in your vault.
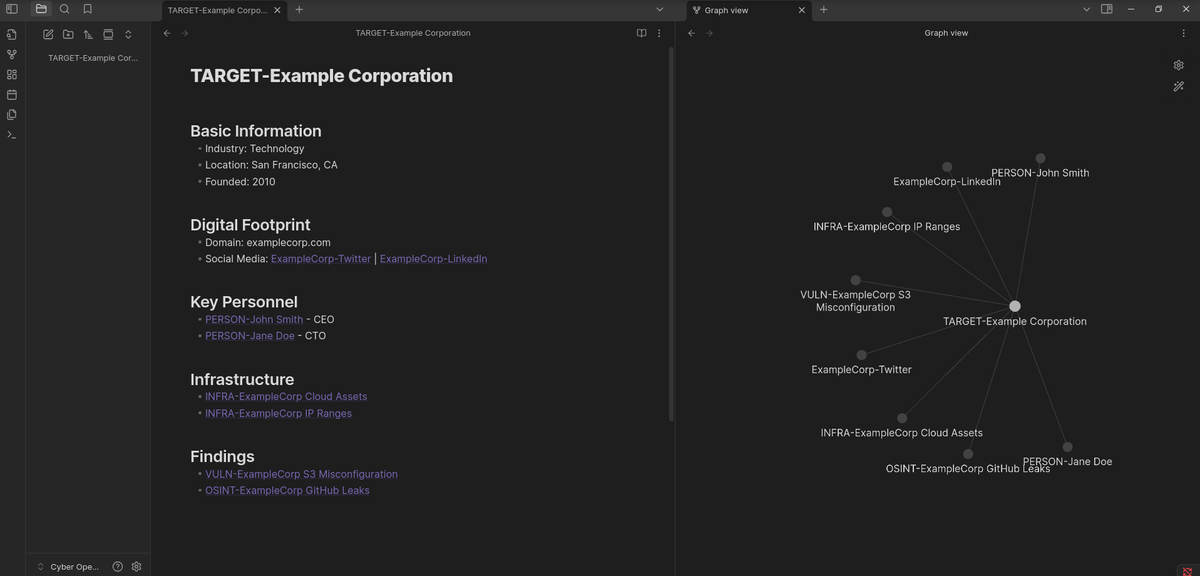
Start by creating a new note for your target – this could be an individual, organization, or domain.
Within this note, document basic information about your target and create sections for different aspects of your investigation. For example:
# # TARGET-Example Corporation
## Basic Information
- Industry: Technology
- Location: San Francisco, CA
- Founded: 2010
## Digital Footprint
- Domain: examplecorp.com
- Social Media: [[ExampleCorp-Twitter]] | [[ExampleCorp-LinkedIn]]
## Key Personnel
- [[PERSON-John Smith]] - CEO
- [[PERSON-Jane Doe]] - CTO
## Infrastructure
- [[INFRA-ExampleCorp Cloud Assets]]
- [[INFRA-ExampleCorp IP Ranges]]
## Findings
- [[VULN-ExampleCorp S3 Misconfiguration]]
- [[OSINT-ExampleCorp GitHub Leaks]]
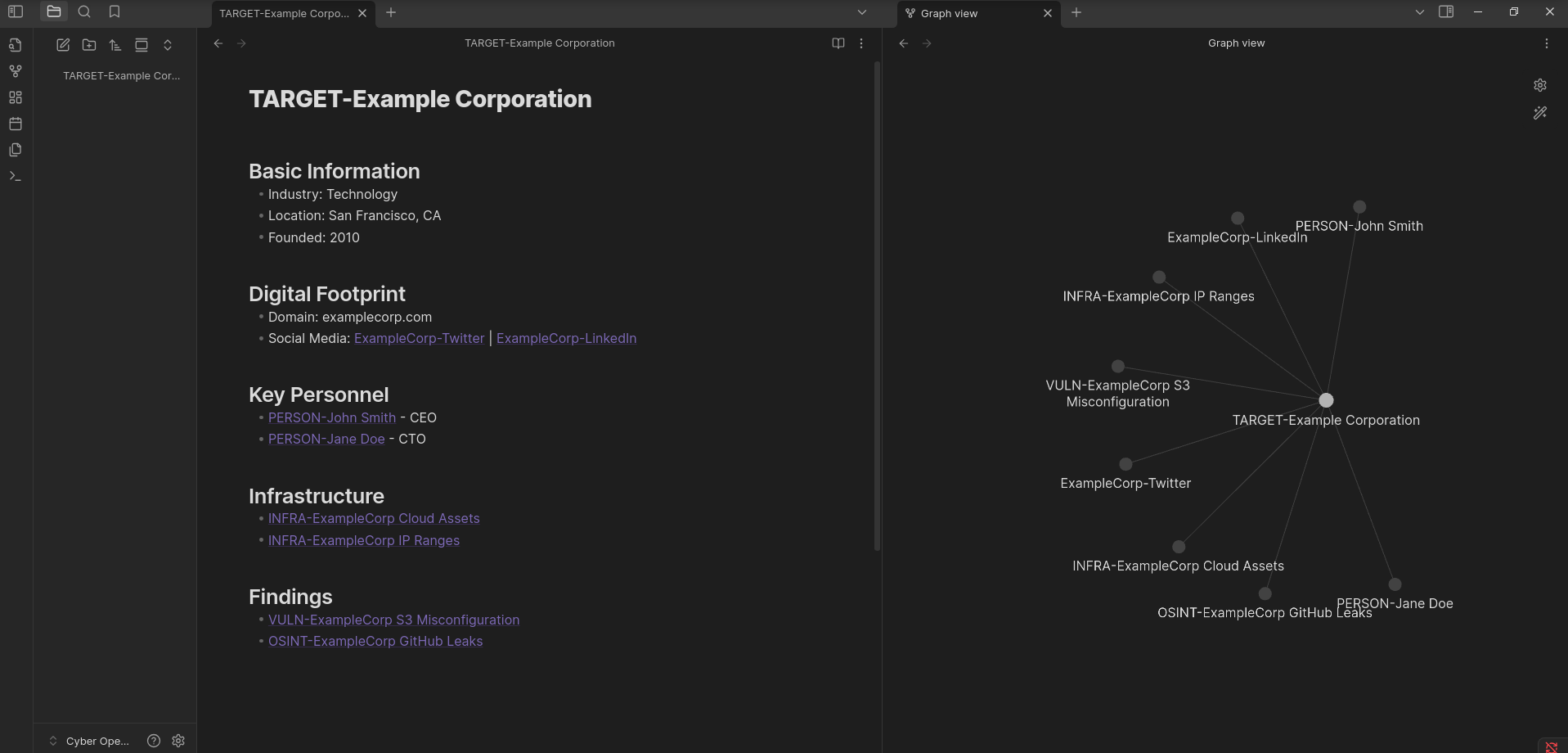
Notice how we're using double-bracket links to connect to other notes. This is one of Obsidian's most powerful features. Each of these linked notes can contain detailed information about that specific aspect of your target.
For example, your "PERSON-John Smith" note might contain information about the CEO's social media profiles, email addresses, public appearances, and connections to other individuals. As you discover new information, you can add it to the relevant note and the connections will automatically strengthen your knowledge network.
What makes this approach particularly powerful for OSINT is the ability to see unexpected connections. Perhaps you're investigating multiple targets and notice they share infrastructure or techniques. Obsidian's graph view can visualize these connections, potentially revealing relationships that weren't immediately obvious.
Step #5 Advanced Obsidian Features for Cyber Operations
As you become more comfortable with Obsidian, you can leverage its advanced features to enhance your cybersecurity workflow.
Plugins
Obsidian's plugin ecosystem extends its functionality in ways that are particularly useful for cybersecurity work:
The Dataview plugin allows you to create dynamic queries across your notes, essentially turning your knowledge base into a database. This is invaluable for creating dashboards that show active investigations, pending vulnerabilities, or targets sharing specific characteristics.
The Excalidraw plugin provides a canvas for creating diagrams directly within your notes. This is perfect for mapping network infrastructures, illustrating attack paths, or visualizing relationships between threat actors.
The Templater plugin supercharges your templates with dynamic content and automation. You can create sophisticated templates that automatically include dates, link to related notes, or even pull in external data.
Encrypted Vaults for Sensitive Information
For particularly sensitive operations, consider creating a separate vault with additional encryption. While Obsidian files are just markdown on your system, you can place your vault within an encrypted container using tools like VeraCrypt for an added layer of security.
Summary
Obsidian represents a paradigm shift in how cybersecurity professionals can organize and leverage their knowledge. By creating a networked knowledge base that mirrors the interconnected nature of security information, you gain insights that might otherwise remain hidden in folder structures or disconnected documents.
Whether you're conducting OSINT investigations, documenting vulnerabilities, developing exploits, or managing security operations, Obsidian provides a framework that enhances your capabilities and evolves with your needs.
Start building your cybersecurity knowledge base today, and watch how it transforms your capabilities in the digital battlefield.