Hacking Tools That You Need To Learn in 2025

“A tool or process can always be better. Nothing is ever complete.” — OccupytheWeb
In today’s complex cybersecurity landscape, security professionals must maintain a deep understanding of both defensive and offensive security methodologies to effectively protect their systems. This comprehensive overview examines six essential tools that form the foundation of hacking.
Shodan & Censys

Unlike conventional search engines that help you find websites and social media profiles, Shodan and Censys venture into much darker territory. These platforms are designed to uncover and catalog every single internet-connected device in the world — from industrial control systems running power plants to unsecured security cameras in homes.
Often referred to as “Google for hackers,” Shodan constantly scans the entire internet, collecting detailed information about every device it encounters. For instance, if a company accidentally leaves a database server exposed to the internet, Shodan will find it. If someone installs a security camera but forgets to change the default password, Shodan knows about it. Its sophisticated search capabilities allow security professionals to find specific types of systems, such as unpatched Microsoft Exchange servers or industrial control systems in a particular country. Shodan even provides historical data, showing how systems have evolved over time.
Censys complements Shodan by providing a more research-focused approach. It collects and analyzes vast amounts of data about internet-connected devices and services, offering security professionals a comprehensive view of the global internet. With its advanced filtering and aggregation capabilities, Censys allows users to identify trends, detect vulnerabilities, and monitor exposed assets. This makes it an indispensable tool for organizations seeking to improve their cybersecurity posture.
Nmap

Nmap, which began its life as a simple network scanning tool in 1997, has evolved into something far more sophisticated. Think of it as the digital equivalent of a master locksmith’s tool set — it helps you understand exactly how a network is put together and what might be vulnerable.
The tool’s name stands for “Network Mapper,” but this humble title barely scratches the surface of its capabilities. At its core, Nmap helps security professionals create a detailed map of any network they’re testing. However, the real magic happens in how it accomplishes this task. When Nmap scans a network, it doesn’t just look for open ports — it attempts to understand exactly what’s running on those ports, what version of the software is being used, and even what operating system the target machine is running.
Nuclei

Nuclei is a powerful and flexible open-source vulnerability scanner designed for security researchers and professionals. It uses customizable templates to identify and report a wide range of vulnerabilities in web applications, APIs, and network services. Nuclei supports integration with other security tools, allowing for seamless inclusion in automated workflows. With features such as rate limiting, custom headers, out-of-band testing, and extensive configuration options, Nuclei provides an efficient and thorough solution for proactive vulnerability management and security assessment.
Metasploit Framework

The Metasploit Framework represents the pinnacle of security testing platforms. While other tools might help you find vulnerabilities, Metasploit helps you understand exactly how dangerous those vulnerabilities really are.
Hackers use Metasploit to verify whether theoretical vulnerabilities present actual risks to their systems. The framework includes a vast library of tested exploits, along with tools for developing and testing new ones. This means security teams can move beyond simply identifying vulnerabilities — they can actually understand how an attacker might exploit them.
Wireshark
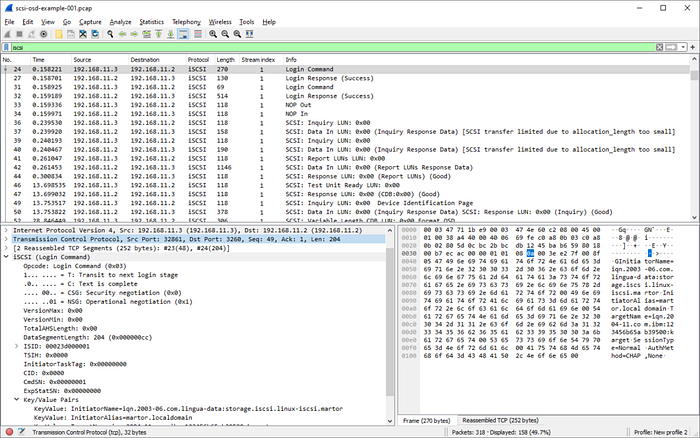
Wireshark stands as the definitive tool for understanding network traffic. While other tools might tell you what’s happening on a network, Wireshark shows you exactly how it’s happening, down to the individual packet level.
Think of Wireshark as a traffic camera for your network, but one that can zoom in to see exactly what’s in each vehicle passing by. When security professionals need to understand exactly what’s happening on a network — whether they’re investigating a potential breach or verifying that sensitive data is properly encrypted — they turn to Wireshark.
The tool’s deep packet inspection capabilities let analysts see exactly what data is moving across their networks. This becomes invaluable during security incidents, where understanding the exact nature of suspicious traffic can mean the difference between containing a breach quickly and letting attackers maintain their foothold.
Conclusion
These six tools represent the foundation of modern security testing and analysis. While there are many other tools available to security professionals, mastering these core tools provides the essential capabilities needed to understand and protect modern networks. Whether you’re defending systems against attack or testing their security, these tools form the backbone of your technical capabilities.
Other articles you may find interesting: