Research & Publications

Vulnerability Scanning: Automatic Search For Known CVEs With CVEScannerV2
This tool enhances the capabilities of the widely-used Nmap scanner, offering security professionals a comprehensive view of their network’s vulnerabilities. Let’s delve into what makes CVEScannerV2 an invaluable asset in the cybersecurity arsenal.

Vagrant: Building Secure Testing Environments
Vagrant simplifies the creation and management of virtual machines through automation and configuration as code. This guide will help you understand Vagrant’s basics and set up your first environment.
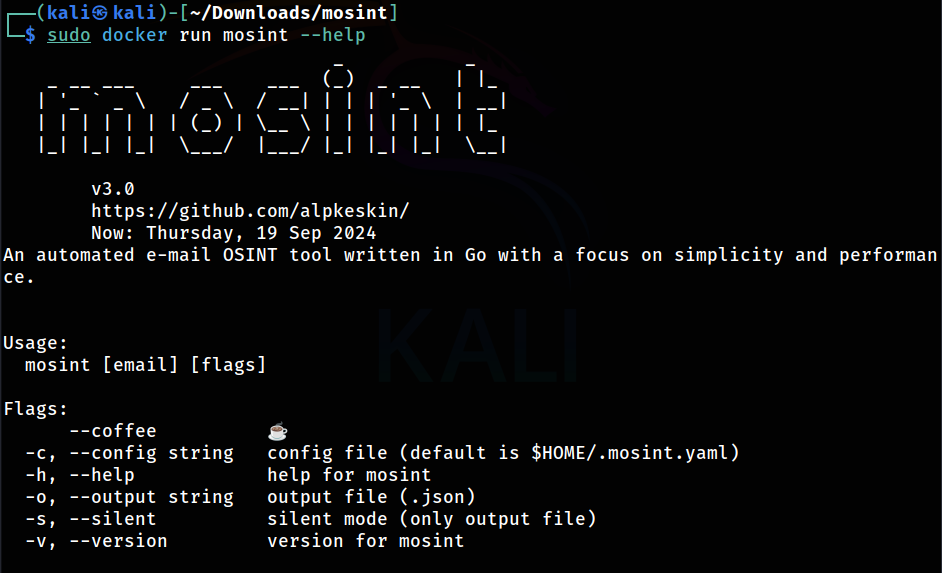
Open Source Intelligence (OSINT): Mosint, The Versatile Email Address Search Tool
As OSINT investigators, pentesters, and hackers, we often need to determine if a target's email address has been compromised in any data breaches. Previously, we looked at h8mail to accomplish this task, but today we'll explore tool that goes beyond – Mosint.
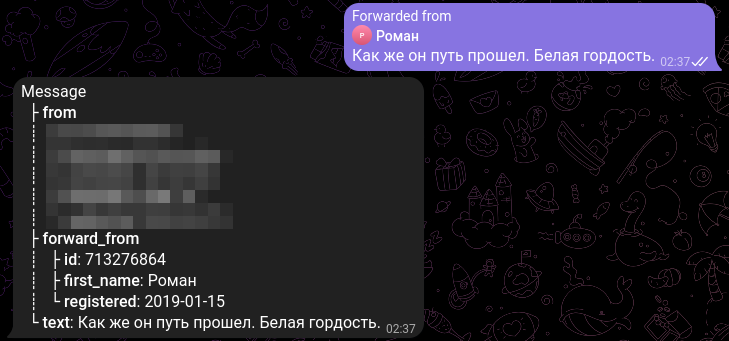
Open-Source Intelligence or OSINT: You Can’t Hide on Telegram!
A lot of people believe that the widely-used social media site, Telegram, offers them anonymity to post confidential information. In this post, we will show you how you can find key information and de-anonymize users on Telegram.

Signal Intelligence with a Software Defined Radio (SDR): The Quiet Revolution in Cybersecurity and Cyberwarfare
This comprehensive analysis explores the technical depths of SDR systems, their real-world applications, and their impact on military operations and satellite communications.

OSINT: Tracking US Spy Planes Surveilling the Mexican Cartels
The U.S. military has increased surveillance activity near Mexico, with spy planes and warships moving closer to the border as part of potential operations against drug cartels. In this article, you'll learn how to use OSINT techniques to track these military movements.

Getting Started with PGP for email
In this tutorial, I will show you how to use OpenPGP in a Tails OS environment to keep your emails pretty private.

Hacking the Cloud: Getting Started
In this article, I reviewed the basics of cloud technologies and their applications. I accessed the cloud and looked around, gaining important information for escalating privileges in the future.

Hacking the Cloud: Privilege Escalation in AWS
It's not always the case that the user whose access you managed to obtain will be an administrator, so it's worth learning how to perform privilege escalation in an IAM environment.

Cyberwar Mission 2: Reconnaissance in the Adversary's Docker Images
Conducting effective information gathering in the Amazon Elastic Container Registry (Amazon ECR)